VPC Peering
VPC Peering is a networking connection between two Virtual Private Clouds that enables secure, private communication using AWS's existing infrastructure without requiring gateways, VPN connections, or separate physical hardware.
- Private Communication: VPC peering allows instances in different VPCs to communicate using private IPv4 or IPv6 addresses as if they were on the same network
- Cross-Account Support: You can establish peering connections between VPCs in your own AWS account or with VPCs belonging to other AWS accounts
- Inter-Region Capability: VPCs can be peered across different AWS regions, enabling global resource connectivity while maintaining private communication
- Infrastructure Utilization: AWS leverages existing VPC infrastructure to create peering connections, eliminating single points of failure and bandwidth bottlenecks
VPC peering connections facilitate secure data transfer and resource sharing across multiple VPCs without exposing traffic to the public internet.
Use case: VPC peering is essential for organizations with multiple AWS accounts who need to share resources, create file sharing networks, or replicate data across regions for geographic redundancy.
How VPC Peering Works
Connection Establishment: A VPC peering connection creates a direct network route between two VPCs, allowing resources to communicate privately without traversing the public internet.
Traffic Routing: Once established, traffic between peered VPCs uses private IP addresses and stays within AWS's global backbone infrastructure, ensuring security and performance.
Encryption and Security: All inter-region peering traffic is automatically encrypted, reducing exposure to common exploits and DDoS attacks while maintaining high availability.
Key Benefits of VPC Peering
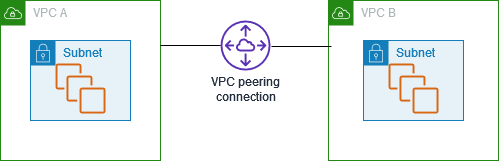
Enhanced Security: Traffic never leaves AWS's private network infrastructure, reducing security risks associated with public internet communication.
Cost Effectiveness: VPC peering provides a simple and economical way to connect VPCs compared to complex gateway solutions or VPN connections.
Geographic Redundancy: Inter-region peering enables data replication across geographic locations for disaster recovery and compliance requirements.
Resource Sharing: Organizations can centralize resources in one VPC while allowing controlled access from other VPCs across accounts or regions.
VPC Peering Configuration Requirements
| Requirement | Description | Considerations |
|---|---|---|
| CIDR Blocks | VPCs must have non-overlapping CIDR blocks | Plan IP address ranges carefully before creating VPCs |
| Route Tables | Update route tables in both VPCs to direct traffic through peering | Ensure proper routing configuration for bidirectional access |
| Security Groups | Configure security group rules to allow traffic between VPCs | Define specific protocols, ports, and IP ranges |
| Network ACLs | Update subnet-level ACLs if they restrict inter-VPC communication | Consider both inbound and outbound rules |
VPC Peering Limitations and Considerations
Transitive Routing: VPC peering does not support transitive routing. If VPC A is peered with VPC B, and VPC B is peered with VPC C, VPC A cannot automatically communicate with VPC C through VPC B.
DNS Resolution: By default, DNS hostnames from one VPC cannot be resolved in a peered VPC unless DNS resolution options are specifically enabled for the peering connection.
Overlapping CIDR Blocks: VPCs with overlapping IP address ranges cannot be peered, requiring careful network planning during VPC design.
Regional Limitations: While inter-region peering is supported, there may be latency considerations and data transfer costs for cross-region traffic.
Best Practices for VPC Peering
Network Planning: Design your VPC CIDR blocks carefully to avoid overlaps and ensure future peering compatibility across your AWS infrastructure.
Security Configuration: Implement least-privilege access by configuring security groups and NACLs to allow only necessary traffic between peered VPCs.
Monitoring and Logging: Enable VPC Flow Logs to monitor traffic patterns and troubleshoot connectivity issues across peering connections.
Documentation: Maintain clear documentation of all peering relationships, especially in complex multi-account or multi-region environments.
VPC Peering Shared Responsibility Model
AWS manages the underlying infrastructure, network availability, and encryption for peering connections, while customers are responsible for proper configuration of route tables, security groups, network ACLs, and access management.